Software is a primary part of our daily routine, every activity now requires some form of computational integration.
The process of software development and use has come to stay in this century, and it’s not stopping anytime soon. The software product development process is a complex one that has been broken down using different intelligent perspectives into organized and precise procedures, step by step, known as the software development life cycle.
The software development life cycle involves all the small processes involved in product management, design, and project management containing all the steps like:
-
Ideation & concept
- Wireframing & prototyping
- Technology selection
- MVP development
- Product development
- Quality assurance & testing
- Cloud & DevOps
- Launch and marketing
- Feedback analysis & improvement
This includes the expected deliverables for a project, rules, and practices, and all the activities carried out to its completion. Deliverable solutions including web and software solutions, software for startups, artificial intelligence and machine learning (AI/ML), blockchain, and the internet of things.
In the software development journey, the product owners trust their development team with the credibility of ownership of the written codes as well as the certainty that the product will work properly. This is a big deal as the authenticity of digital products is being pushed gravely across all industries with huge repercussions for companies with products developed on possibly stolen codes.
In this article, we explain the need to secure software codes and the use of blockchain technology in achieving this security.
Why Do You Need To Secure Code?
In these days of fast software development launches, there’s the rapid surge of digital solutions in the market and the need for creators of these digital solutions to protect them and guard them against common software vulnerabilities. These concerns include the following:
-
When codes are not secure, the end-users (consumers) of your product may get security warnings that discourage software downloads.
-
The launched digital product (software solution) may get withdrawn completely based on unauthorized use of code.
-
Exposure to lots of legal breaches and the complicated phase of clearing them.
-
The negative impact of software vulnerability exposure on the product as well as the company.
-
Codes are written daily for these product launches, and it is becoming difficult to prove ownership of these written codes.
Code Ownership
Startups, enterprises, product companies, as well as other small & big companies with digital software products are required to prove code ownership for the products they launch to the digital market. Inability to produce this has resulted in high-profile cases running in billions of dollars. Hence, software outsourcing companies, in-house or offshore now put in the extra work, signing outsourcing contracts to assign ownership of code, and use various technological processes in securing these codes used in bringing product solutions to life.
This means that the software development partner has to write this code themselves, not copied from other sources, and prove that they wrote it themselves. If a software development company assigns code ownership of a code they didn’t write to a client, then that is code theft, malpractices that can lead to a lot of legal complications involved.
There are different factors considered in the code ownership journey:
-
The software programmers or remote developers you hire adopt processes to store all transaction records securely.
-
The developers sign the codes to prove ownership, code signing is different from SSL.
-
The entire development process should have a clear trail of dates and time stamps.
The times are changing, and software companies are adopting various technological processes to prove code ownership - one of these processes is the use of blockchain technology.
What Is Blockchain Technology?
Blockchain technology is a technology built on the use of data structures, cryptographic, with immutability, consensus, decentralization, and inherent security qualities that ensures the authenticity of transactions. The blockchain technology process is the foundational system on which bitcoin and other digital currencies are built. Software development companies have found a way to use this decentralized system to prove code authenticity, ownership, and ensure the security of digital products.
Also Read: 16 Amazing Examples of How Blockchain Technology Helps In Real Life
The data structures in blockchain technology are stored in blocks, these blocks are connected in a cryptographic chain format which guarantees security. Furthermore, the decentralized system process ensures all transactions within the block of data are only validated by the participation of members by a consensus mechanism. The seeming complexity of the blockchain technology process is what makes it nearly impossible to infiltrate and tamper with.
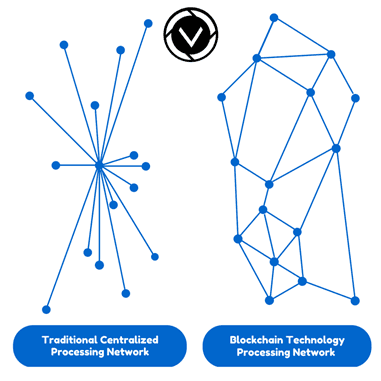
Blockchain technology runs on some basic principles that ensure the security of the network.
-
The use of a decentralized system ensures there are no central servers. This means there is no way to compromise all servers and disrupt the mechanism of the network or alter existing data.
-
The use of a “peer-to-peer” (P2P) network in transaction processes.
-
The use of modern data encryption technology enables digital signatures used by all participants to sign transactions.
-
Cryptographic chain format secures individual data blocks on the network.
-
The immutable records collect trails of dates and timestamps which also include the author’s details.
The use of blockchain technology in software security - blockchain security provides a comprehensive tamper-proof system that thrives on cybersecurity frameworks and cryptographic protection.
Securing Codes With Blockchain Technology
The outlined principles of blockchain technology prove that the system holds an immutable database. This means the use of blockchain technology in code security is tamper-proof, and you can easily prove ownership of your company’s written codes, as well as identify code-theft culprits. You can even hire blockchain developers to infuse the power of blockchain in your software while also securing the codes using this tech.
Here are some practical tips in securing codes using blockchain technology:
-
Segmentation. Choose what data you want to be captured on each data block.
-
Identity management. This ensures encryption processes and the block key management processes. In securing your code on the blockchain, you need to choose whether to reveal the content of the code or not to reveal the content of the code (using the zero-knowledge-proof technique).
-
Access to the network. Choose the participants who have access to your data. Whereby you can label your blockchain network as private or public granting identity access and permission control as preferred.
-
Disaster recovery. Develop a disaster recovery template for participatory members.
-
Maximum security. Create your security and risk model on the existing blockchain system to ensure the security of your solutions and protect against governance, business, and technology risks.
-
Control system. Establish and define security control across your blockchain network to guard trust, privacy, and security.
On successfully securing ownership of your codes as transactions on the blockchain, you can set up smart contracts with conditions allowing only authorized parties access to use your code.
Adopt Blockchain Technology Process In Securing Your Codes
The use of blockchain technology in software security is new but has proven widely beneficial in different processes. Although a comprehensively complex procedure at the moment, it is still evolving into different segments, all to provide tamper-proof security across all industries. Hence, you must find a software development company with blockchain development solutions, like Classic Informatics, to build products and secure your code ownership for all digital content.













.png)